So why would you want to use SSH tunneling? Here are a few common purposes:
- bypass restrictive web filters or firewalls :)
- encrypt unsecure data (e.g. email traffic); prevent eavesdroppers
- use your home internet connection from abroad
Today I will show you how to construct your own SSH tunneling system setup, accessible from anywhere you have internet access. The system is composed of two parts: the SSH server (I will show how to set this up on a Linksys WRT54G/GS router using Tomato firmware) and the portable USB toolkit, which will be composed of the Portable versions of the PuTTY SSH client and common internet applications, such as the Portable Firefox browser or Pidgin IM client.
What You Will Need
- Linux-based Linksys WRT54G/GS/GL router (beware of the castrated VxWorks-based models!)
- Tomato router firmware
- Home/office broadband internet connection (1.5Mbps or greater works well)
- a DynDNS account (so the router can have an easy-to-remember hostname)
Part 1 - Set up the SSH Server
Using the router as the SSH server is the most practical option, for several reasons. First, it is always-on and reliable, considering that the average person does NOT run a dedicated always-on server in their home. Second, configuration is naturally easy since the router is already hooked up to the internet connection.
I recommend Linksys routers because they are probably the most common home router out there, and because they are ridiculously easy to hack (Linksys released the specs under the GPL!)
This is where custom firmware comes in – adding extra features and capabilities, such as the embedded Dropbear SSH server we will be taking advantage of. I recommend Tomato because I have found it to be one of the lightest and fastest firmwares (the slick SVG graphs don’t hurt, either).
Flashing the firmware (if you aren’t already running some form of third-party firmware) is relatively straightforward and will not be covered in this tutorial. To put it bluntly, if you can’t figure out how to do it, it’s probably not the brightest idea to continue…
Port 443 is typically used for HTTPS, and is usually left open even in web filters and firewalls due to its widespread use on the internet (think banking, shopping, secure websites, etc.) Since both SSH and HTTPS are encrypted protocols the filter/firewall won't be able to tell what the traffic really is...are you managing your bank account, downloading porn, surfing YouTube? To a filter or firewall, it's all good.
The next step is to set up the dynamic DNS. Register for a free DynDNS account.
In the DynDNS account manager, create a new IP redirect hostname.
Go back to your Tomato web interface, and go to the Basic->DDNS menu.
Input your DynDNS username, password, and hostname. See the image below for recommended options.
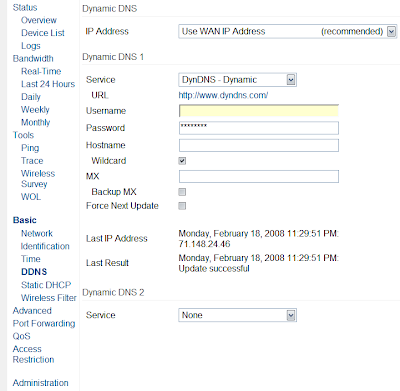
With the dynamic DNS, you will have an easy-to-remember hostname that you will use to connect back to your router.
When we continue in Part 2, I'll detail how to set up a USB drive with portable programs to use your SSH tunnel anywhere, anytime.




No comments:
Post a Comment