In my earlier post, Retrieving Windows Passwords Through Backtrack 3, I outlined the process of obtaining the Windows login password hashes. Obviously, those hashes are encrypted, so naturally we come to the next step - password cracking. There are several methods of attacking password hashes:
- dictionary attack - run the contents of a wordlist against a password hash for matches
- brute force attack - compute and try all possible password combination and see if it matches your hash
- hybrid attack - combines dictionary and brute force methods (permutating the wordlist)
- rainbow tables - trades off disk and memory space for time: all possible combinations are precomputed and stored in large files, which can be rapidly scanned to find a match for the hash
For the vast majority of Windows passwords, rainbow tables work great. ophcrack is a great n00b-friendly solution as the client is small and easy to install; additionally, rainbow tables for alphanumeric tables are freely available and are claimed to have a 99.9% success rate.
- Step 1 - Download and install the ophcrack client + tables.
- http://downloads.sourceforge.net/ophcrack/ophcrack-win32-installer-3.0.1.exe
- At the tables download screen, download:
- WinXP small (380MB) if you have less than 512MB of RAM and want to crack LM hashes
- WinXP large (703MB) if you have more than 512MB of RAM and want to crack LM hashes
- Vista tables (461MB) if you want to crack NTLM hashes (default hash type on Vista)
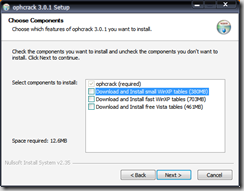
- Note: You may also manually download and install the table files.
- Step 2 - Check ophcrack settings
- Open ophcrack and check the Tables button and the Preferences tab.
- Ensure that the table(s) you downloaded are enabled with a green icon.
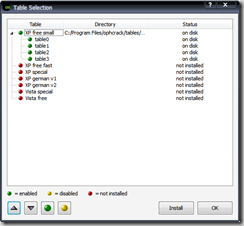
- In Preferences, ensure that the number of threads is equal to the number of processor cores you have.
- Step 3 - Load the password hashes.
- If you used my Linux-based dumping procedure or a tool such as pwdump or fgdump, select PWDUMP file from the Load button.
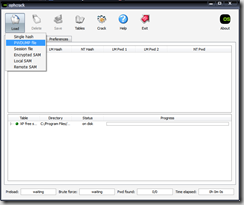
- You may also input a single hash or load the SAM from the local computer.
- Step 4 - Begin cracking!
- This is the easy step - once the hashes are loaded, simply press Crack. If all goes well and the passwords are alphanumeric only, you should have the decrypted password under the NT Pwd column within 10 minutes or so.
- Here is a screenshot of some successfully decrypted passwords - three simulated, relatively strong passwords that were cracked in only 26 seconds using the XP small tables on a machine with 1GB RAM.
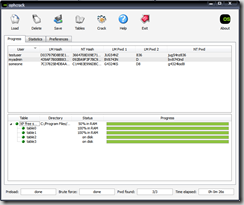
It is a common belief that the NTLM hash algorithm is much more secure than the older LM algorithm used in Windows 2000 and XP. However, the ready availability of the Vista/NTLM rainbow tables puts this oudated belief to rest. With rainbow tables, even attackers with run-of-the-mill PCs can mount an effective attack against Windows passwords. GUI tools like ophcrack only simplify such efforts. Advice for the whitehats and the security-minded? Use a long password - on Windows 2000/XP, NTLM must be used if the password exceeds 14 characters due to limitations in LM. Furthermore, long passwords deter brute force attacks. Make sure you don't use a common word in your password, as this is easy prey for dictionary attacks.
Additionally, use a symbol or two in your password, as this will automatically render alphanumeric-only rainbow tables useless. Similarly, brute-force and dictionary attacks will be made much more difficult due to the vastly expanded search space.
From a larger perspective, we again demonstrate the weaknesses of Windows password hashing algorithms. Again, have more than one layer of protection - encrypt your data, set a BIOS passwords, etc. A compromised password = compromised data.



No comments:
Post a Comment