WARNING: The procedure outlined here is NOT intended for casual n00b users. If you don't get it, don't do it. Experience with Linux is highly recommended to understand this tutorial.
Let's say that you forgot your Windows password...or that you need to get at another user's for legitimate (pentesting?) purposes. Assume the following:
- The Windows installation has passwords on all local accounts, including the administrator.
- As a result, you will not be able to use Windows to recover the password hashes.
So what now? The solution is to use another operating system to gain access to the Windows partition on the hard drive. Linux, with its now-strong NTFS support, is ideal for this task. Today, I'll be showing you how to use the Backtrack 3 Linux distribution and samdump2 to access and dump the SAM file on Windows XP and Vista. The instructions that follow detail installing BT3 on a USB stick through Windows - if you're going for your own password, then have another computer available.
Obtain and install Backtrack 3 onto a USB drive (not CD!)
- You will need a 1GB or larger drive.
- http://www.remote-exploit.org/backtrack_download.html
- Extract the downloaded ISO file to the root of your USB stick using something like WinRAR or IZArc.
- Navigate to the boot directory. Run bootinst.bat to install the bootloader on your USB. Make sure you run this from your USB and NOT from your local hard drive - otherwise, you will end up not being able to boot Windows anymore!

Install samdump2 v2.0.
- samdump2 is a Linux tool for decoding the Windows SAM file and undoing SYSKEY encryption. Backtrack 3 actually contains version 1.1, but this version is comprised of two separate programs which is less user-friendly. The latest version combines both SYSKEY decryption and SAM reading into one program.
- I have compiled an LZM module which will update Backtrack 3 with the latest version. Put the module file in BT3/modules.
Start BT3.
- Restart your computer and boot to the USB device (you may have change your BIOS boot settings).
- You should see the following menu:
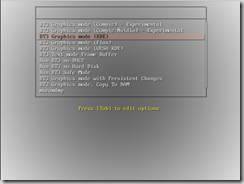
The fancy Compiz graphics are not needed. In fact, we could do with just a command prompt. I recommend choosing either BT3 Graphics mode (KDE) or BT3 Text mode Frame Buffer. - If Backtrack 3 does not automatically login, use root and toor as the username and password, respectively.
Perform the dump.
- If you are using graphical mode, open a shell window from the menu bar.
- Type df. This command gives you a listing of all mounted filesystems. Your Windows partition should be among the output; make note of the corresponding device name "Mounted on" column - for example, hda1 from /dev/hda1.
- Now enter cd /mnt/DEVNAME/WINDOWS/system32/config. Replace DEVNAME with your device name - I am using hda1 in the example, so I would type cd /mnt/XXX/WINDOWS/system32/config.
- Type ls to list the contents of this directory. Verify that the files SAM and system among the listing.
- Now type samdump2 -o ~/winhashes.txt system SAM to undo the SYSKEY protection and dump the SAM. A copy of the hashes will be stored to winhashes.txt in the user home directory.
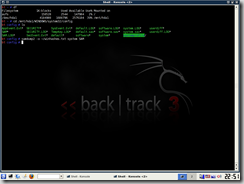
- Simply copy this text file to your same USB stick or use Backtrack 3's Firefox to email or upload it.
- The hash file (see below) is in standard pwdump format. Many password-cracking tools can handle this, such as John The Ripper and ophcrack.
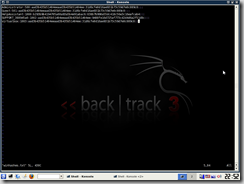
This method demonstrates Windows' inherent lack of password security. By default, Windows NT, 2000 and XP store the hash using LM, which is quite insecure and easily defeated. Windows Vista uses the more secure NTLM hash. But regardless, make sure you use a strong password that is reasonably long and contains numbers and/or symbols. However, password-dumping attacks like this can be effectively thwarted by setting a BIOS/boot password so that the computer cannot be started without authorization. It is fair to say that many or most people have no such security on their computers short of locking their computers when they go out. Unfortunately, though, the Windows password provides a false and inflated sense of security and privacy.



2 comments:
How did you compile samdump2 v2.0 for BT3? I downloaded the source code, compiled it, and when it runs it gives me the hashes, but then it segmentation faults.
Thanks,
Will this work for 2008 Server?
Post a Comment